Replace Legacy VPNs with Cloud-Native Zero Trust Network Access
Zscaler is a leading cloud-native security platform that enables fast, secure connections and empowers organizations to embrace digital transformation.
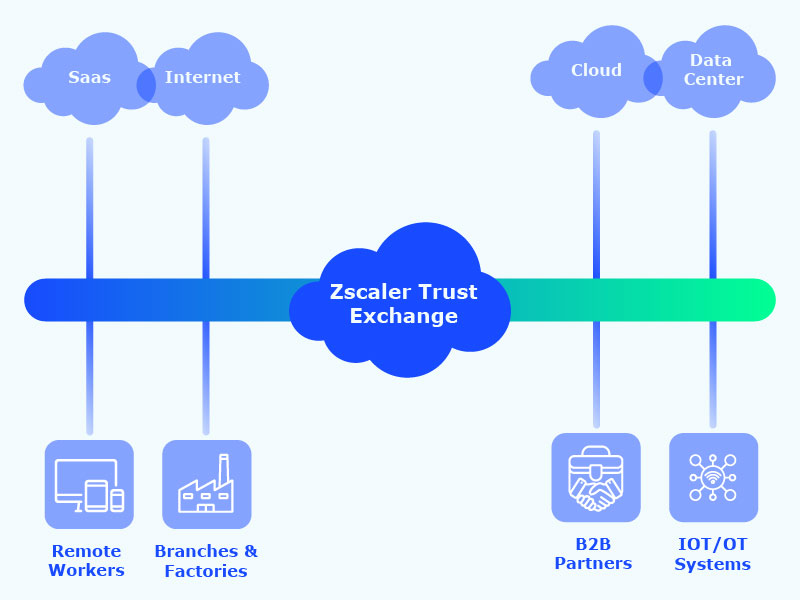
Built on a zero-trust architecture, Zscaler provides secure access to applications and services—regardless of user location or device. Trusted by thousands of global enterprises, Zscaler eliminates the need for traditional on-premise security appliances, simplifying IT operations and reducing risk.
Why choose Zscaler? Faster Performance, Stronger Security, Zero Compromise
Zscaler's Zero Trust platform connects users securely to authorized apps with 50% less latency, eliminates complex VPN infrastructure, scales automatically with business growth, and delivers consistent security and performance for office, remote, and hybrid work environments.
- Zero Trust Security – Users connect only to authorized apps, minimizing the attack surface and lateral movement.
- Improved User Experience – A direct-to-cloud approach reduces latency and improves application performance.
- Reduced IT Complexity – Eliminates the need for VPNs and traditional security hardware.
- Scalable & Agile – Cloud-native design supports fast deployment and scales with your organization’s needs.
- Secure Remote Work – Ensures safe access for remote and hybrid teams without sacrificing performance or protection.
Protect your organization from the new generation of threats - Zscaler's key features
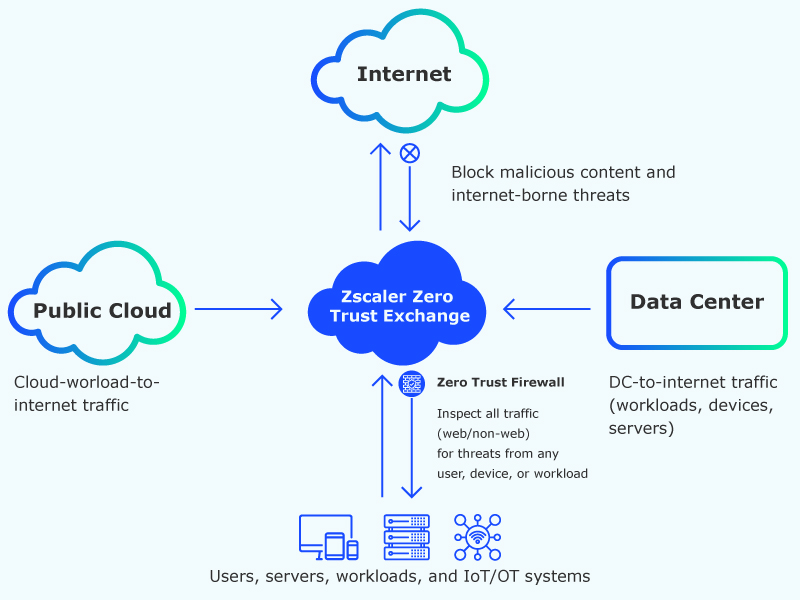
Zscaler's platform combines secure internet access (ZIA), private application access (ZPA), integrated cloud firewall, advanced sandboxing for threat protection, and comprehensive data loss prevention with cloud security broker capabilities for complete enterprise security.
Zscaler Internet Access (ZIA)
Secure all internet traffic with cloud-delivered threat protection and data loss prevention. Real-time inspection blocks malicious websites and prevents data exfiltration without on-premises hardware.
Zscaler Private Access (ZPA)
Provide secure access to internal applications without VPN complexity or internet exposure. Software-defined perimeters create encrypted micro-tunnels based on user identity and context.
Cloud Firewall
Sandboxing & Threat Protection
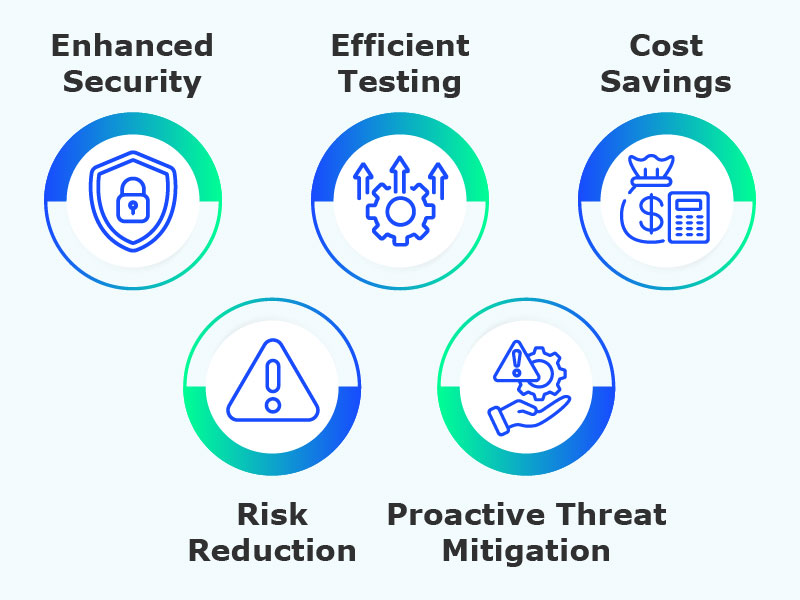
This approach delivers key benefits:
- Enhanced Security
_ Efficient Testing
- Cost Savings
- Risk Reduction
- Proactive Threat Mitigation
Cloud DLP & CASB
Complete data protection and cloud service visibility with automated compliance enforcement. Monitor data movement and cloud application usage while maintaining regulatory compliance.